Pulumi, Terraform, and CDK are Infrastructure as Code (IaC) solutions — tools that help manage IT infrastructure via software-defined rules by defining resource configurations. They enable your development and operation teams to build, change, and provision compute resources more efficiently in a safe, consistent, and automated way.
IaC is a key element of Agile methodology and DevOps practices. It enhances source control, continuous integration, and continuous deployment. It also helps you make experimental changes without investing too much time or resources.
Terraform
Terraform is an open-source IaC tool that lets you define infrastructure via human-readable, declarative configuration files. It’s one of the most widely used automation tools for multi-cloud deployments.
You can express the infrastructure configuration using scripts written in HashiCorp Configuration Language (HCL) and, optionally, JSON format. Terraform looks at scripts you write, compares them to the existing state, and makes changes to the infrastructure.
Pulumi
Pulumi is a multi-language platform that lets developers provision infrastructure with general-purpose programming languages. Like Terraform, Pulumi is open-source and cloud-neutral — it allows you to define resources on numerous providers (including Azure, Google Cloud, and AWS).
AWS Cloud Development Kit (CDK)
AWS CDK v2 is an open-source development framework for deploying infrastructures via AWS CloudFormation. It’s similar to Pulumi in the way that it lets you use multiple programming languages to define your environment.
CDK is a wrapper for CloudFormation. When you run applications on CDK, they compile down to fully formed JSON and YAML templates for provisioning. It also offers some of the features of CloudFormation, like automatic rollback and drift detection.
This is just a general overview. Let’s examine these tools closely in the context of their technical specifications and use cases.
Programming language

Pulumi and AWS CDK let you choose from a range of widely-supported programming languages. Your team can follow these languages' functions, statements, loops, and conditionals to create dynamic cloud environments.
Notably, you need to install a JavaScript runtime to use AWS CDK. That’s because it builds its business logic in TypeScript to ensure consistent behavior of constructs for different programming languages.
Unlike CDK and Pulumi, Terraform uses a high-level proprietary language called HCL. This language has a simple syntax, which makes it easy to provision the infrastructure on multiple cloud and on-premise data centers. Additionally, you can also translate HCL into JSON.
Terraform is sharpened for cloud provisioning and offers great efficiency in skillful hands. Plus, HCL doesn’t take long to master for senior engineers.
Pulumi and CDK are more convenient for most companies because they let them use popular native languages. Your operations team can follow the same development methodology and standards as the development team. Additionally, these tools allow reusing the same libraries across infrastructure and application code.
Terraform and Pulumi are particularly valuable for companies that manage a multi-cloud infrastructure. At the same time, AWS CDK only works with Amazon’s cloud services.
Integrated development environment
Terraform, Pulumi, and CDK support numerous integrated development environments (IDEs) for coding. You can use plug-ins to validate documents, highlight syntax, check for compile-time errors, and to add other visual editing features.
These IaC tools have plug-ins that facilitate on-premise and cloud infrastructure. They let you enforce logic-based and role-based policies for your infrastructure, audit logs, and monitor resource operations. Some plug-ins allow these IaC tools to work together and enable self-service automation.
IDEs can expand supported programming languages. For example, you can install cloud development kits to provision infrastructure on Terraform using TypeScript, Java, Python, or C# (among others).
State management
CDK and Terraform use state files to store metadata about your resources and configuration. However, your operations team must ensure the states are in sync with the infrastructure at all times.
Terraform Cloud and Pulumi have user-friendly web applications that automatically manage the remote state of your infrastructure. So, even if you don’t have a self-managed backend, the built-in service will take care of the state management, security, auditing, and other concerns.
With Terraform and Pulumi, you can manage the infrastructure state manually on compatible cloud storage or local file systems. But if you use AWS CDK, the CloudFormation service will handle the state management.
Cloud compatibility
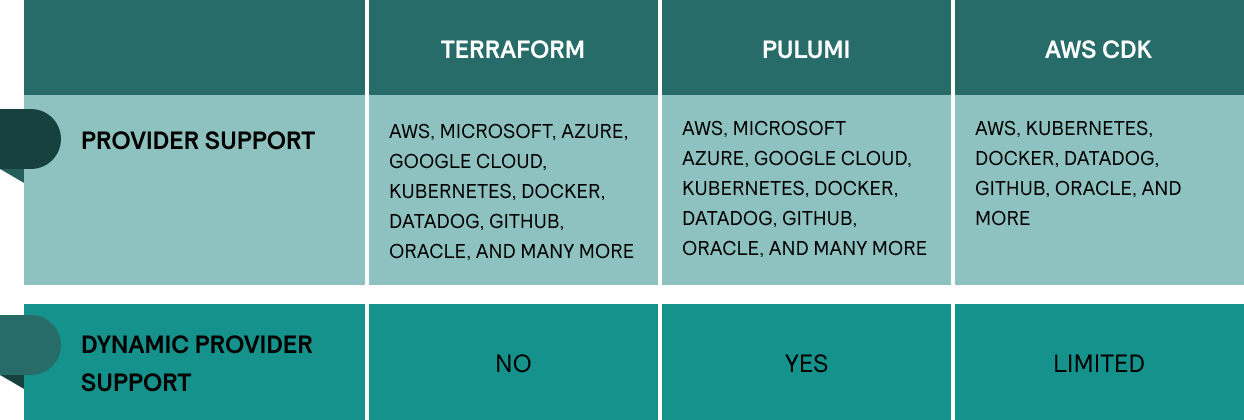
These IaC tools allow you to enhance their functionality with third-party cloud providers via APIs. Pulumi and Terraform support Google, Azure, and AWS. As Amazon’s product, CDK offers a full range of AWS services with limited third-party support.
Each of these tools lets you simplify Kubernetes provisioning. Particularly, you can automate the deployment of applications into your cluster on cloud platforms.
It’s possible to extend your system to include custom resources (if the IaC doesn’t cover your third-party service). However, only Pulumi has full Dynamic Provider Support — it can generate credentials for providers, meaning your team doesn't have to spend as much time writing complex modules.
Testing and validation
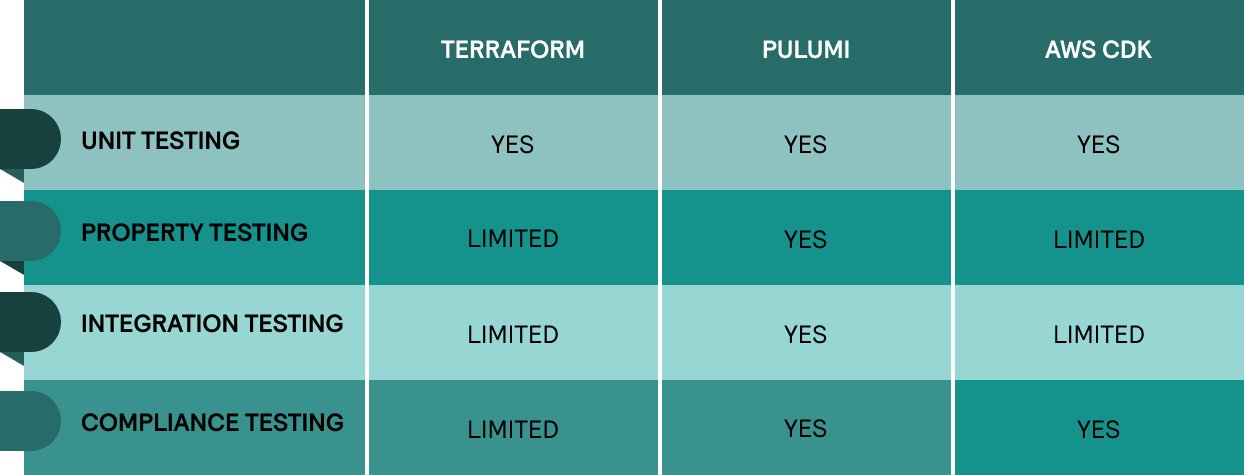
Terraform, Pulumi, and AWS CDK support syntax checking and validation. They also let you run in-memory tests that mock external calls (unit tests) for direct debugging. You create an execution file alongside the configuration files for all infrastructure changes before deployment. Once verified, you can apply the execution plan.
Pulumi makes it easier to assert data flow across resource dependencies while on the deployed infrastructure (property testing). You may also run external tests against the whole IT environment (integration testing).
You can write two categories of tests for AWS CDK constructs: snapshot tests and fine-grained assertions. The snapshot tests compare your synthesized CloudFormation template against the previously stored template (you use them as the baseline for future tests). Assertions can detect regressions when you’re developing new features in your environment.
Additionally, you can install external libraries to enhance your testing functionality. An example would be Terratest for Terraform, which adds a variety of testing for the Go language. Or, take this tool that adds compliance testing into the development pipeline.
Configuration management
You can use traditional configuration management tools within your computer instances. Ansible, Chef, Puppet, and similar services are available on all of the IaC tools. And although AWS CDK, Terraform, and Pulumi aren't made for configuration management, they offer some degree of configuration, too.
Pulumi lets you store secrets and stack variables in configuration files. With Terraform, you can create a file that provides default values for each server to override default configuration values. It's also possible to create default tags for each resource in AWS CDK.
Integration with DevOps tools
Pulumi, Terraform, and AWS CDK integrate with existing continuous integration and deployment (CI/CD) pipelines. This includes popular solutions like Azure DevOps, AWS Code Services, Google Cloud Build, and GitHub.
In addition to third-party integration, AWS CDK has a self-updating pipelines construct library module which integrates continuous delivery. Similarly, Pulumi has several built-in features to facilitate your pipeline, such as deployment, drift detection, and Git commit tracking.
Modularity
All IaC tools let you raise the level of abstraction for resources and constructors to make them reusable.
In Terraform, you define modules using input variables, output values, and resources. Modules can call other modular blocks, but over-using this can make your configuration harder to maintain. You can also enable a no-code provisioning workflow in the Terraform Cloud to deploy module resources without excessive coding.
AWS CDK also allows you to reuse infrastructure elements via CloudFormation. As with Terraform, CDK lets you nest these blocks into other modules to stack your best practices into higher-level blocks. So, you can create your infrastructure standards across modules.
You can abstract Pulumi’s component resources into higher-level software resources with their own logical names and trackable states. It lets you do this by building on top of your programming language. However, the Pulumi Packages plug-in lets you make these modules accessible in any of the supported languages.
Resource naming and tagging
You can establish consistent naming conventions for your cloud resources. Pulumi, Terraform, and CDK allow changing the logical name and tag of any resource in specific modules.
All tools support resource renaming and let you change their parents (moving to other components). However, Terraform doesn’t support declarative changing of the resource’s underlying type or workspace.
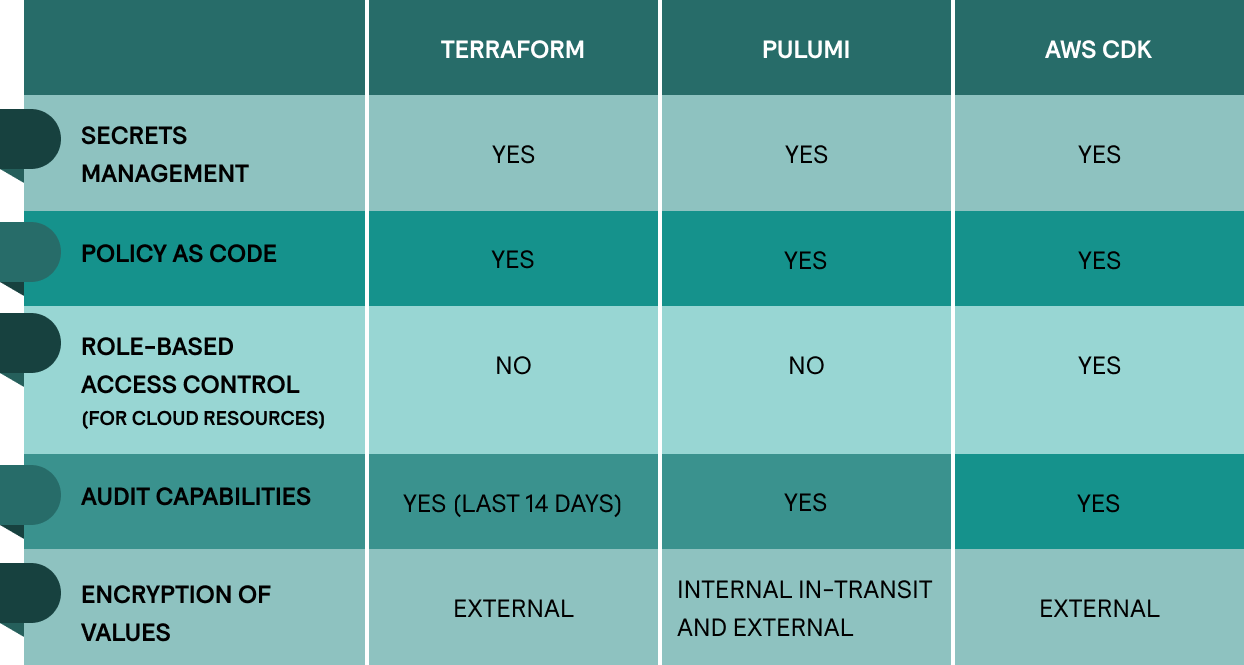
All providers natively support a variety of backends that you can use to store secrets. Many of these solutions support top-grade encryption standards (AES 256-bit), so you don’t store your credentials in plain text.
Similarly, these IaC tools allow you to use code to manage the rules and conditions of your infrastructure. The only tangible difference is that Terraform requires you to use its proprietary language.
You can track user-related activity within your organization with all providers. The logs capture different events and application changes along with timestamps and the users who invoked them. Sadly, Terraform Cloud retains only the previous 14 days of logging information.
Pulumi has integrated encryption for files in transit and at rest. It also makes sure anything the secret interacts with (state files, logs, and CLI outputs) gets automatically encrypted. In comparison, Terraform and AWS CDK lack built-in support for secret management.
Documentation and support
AWS CDK, Pulumi, and Terraform offer vast libraries of technical documentation and extensive guides for various cases. They serve to help you provision your IT infrastructure, employ software engineering practices, and share design patterns among your teams.
Additionally, these IaC tools are also open-source. They are backed by large communities that build plug-ins and libraries that enhance their functionality.
Still, Pulumi and AWS CDK are comparatively new tools. They have growing communities but it’s not as vast as Terraform has. For example, there are far more Stack Overflow questions for Terraform and CDK than there are for Pulumi.




