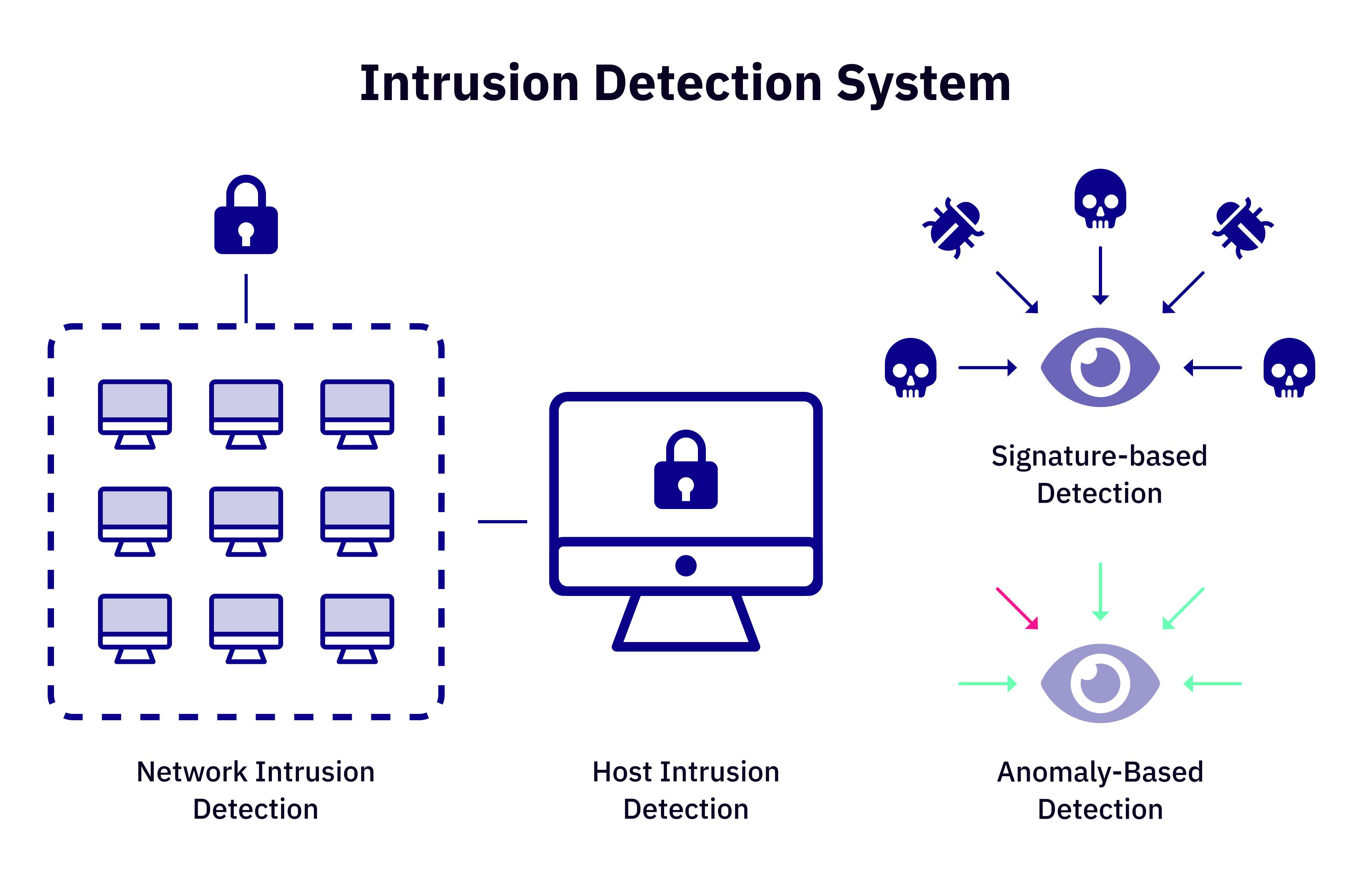
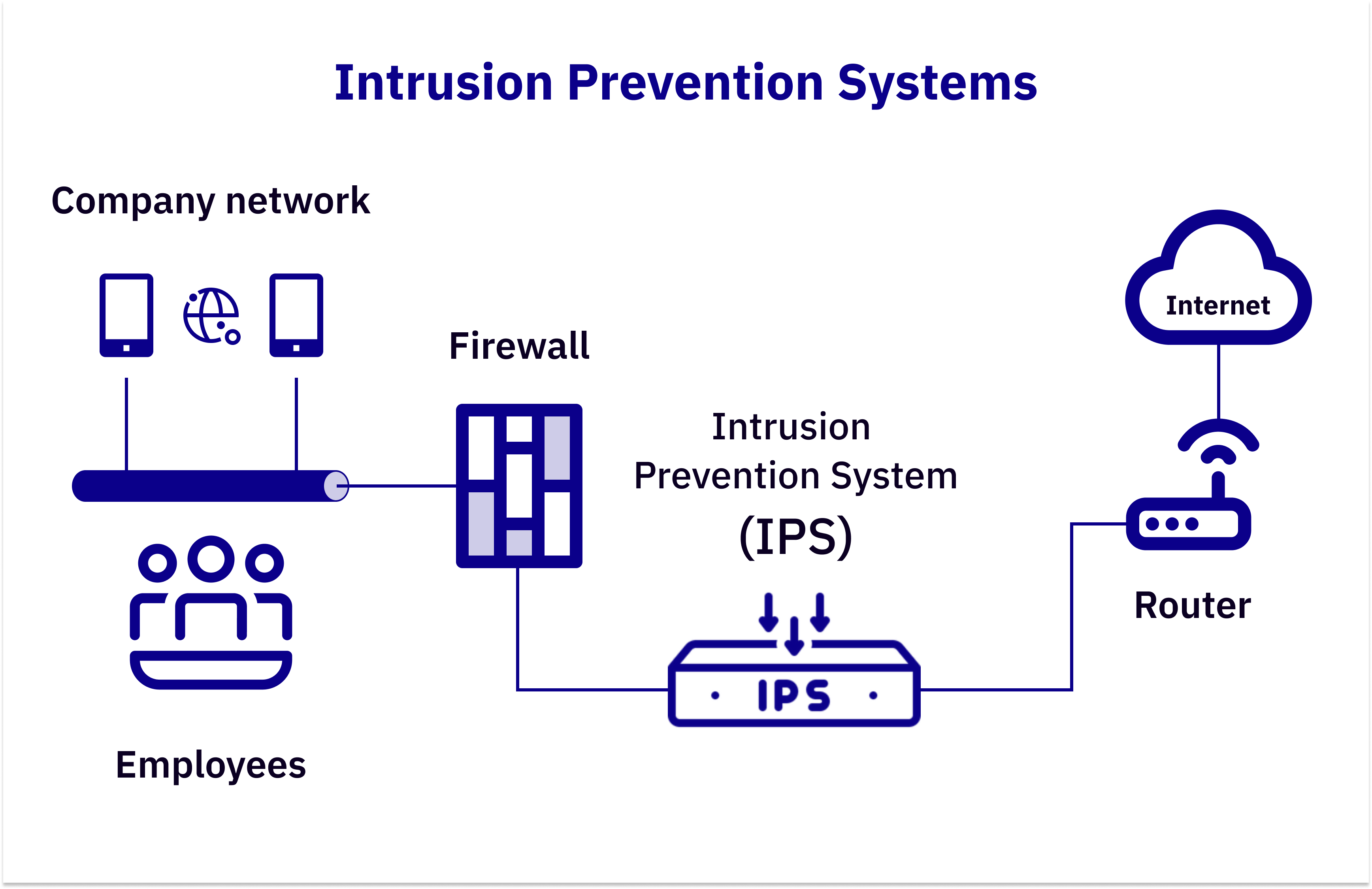
Here are the most popular tools designed to protect your cluster and containerized applications from intrusions, zero-day exploits, and other anomalies.
1. Aqua
The Aqua CNDR platform provides detection, prevention, and response automation tools across your entire K8s infrastructure. It uses behavioral detection and eBPF (Berkeley Packet Filter) to detect network attacks, evasion techniques, and unrecognized malware.
This solution can be a great help to DevSecOps teams. Aqua CNDR assesses and scores your workloads to help your specialists identify vulnerable deployments, so you can prioritize mitigation efforts. It also lets you map out the inbound and outbound connections for each deployment, helping you identify likely entry points for attacks.
Aqua also identifies containers that didn’t come from your pipeline or were changed after deployment. Doing so helps you block containers and suspicious authorization attempts.
On the other hand, the platform lacks granularity in role-based access control (RBAC). So, you need to set permission for each cloud integration manually. It also doesn’t group alerts, which is troublesome for enterprises with a large number of microservices.
2. Datadog
Datadog monitors every node in your K8s, even if they’re distributed across several clouds. It detects attacks against infrastructure, monitors clusters for security misconfigurations, and automatically reports on CIS benchmarks. In addition to IDS, it tracks resource metrics (like CPU, memory, and traffic load) and logs autoscaling events.
This software supports over 500 integrations with common monitoring and log management tools for real-time visibility into your infrastructure. You also get application performance monitoring (APM) and distributed tracing for transaction-level insight into your activities. All reports and logs are automatically tagged and grouped for your convenience. For instance, logs from your Redis containers will be tagged as service:redis and source:redis.
Sadly, Datadog lacks comprehensive documentation for its integrations and configurations. Even worse, its billing panel doesn't show how much you owe until the end of the month, which plays a dirty trick with your budget. Plus, you can’t set caps and limits, so there’s no way to know how much they'll charge you.
3. Falco
Falco is an open-source cloud-native runtime security tool for threat detection across Kubernetes. You can run it directly in K8s or isolate it for extra protection in case of a breach.
This system continuously monitors your cluster and cloud logs to detect unexpected behavior, configuration changes, or possible data leaks. It can also spot abnormal activity and intrusion based on Kubernetes audit logs, system calls, arguments, and properties of the calling process.
It’s a trendy solution with many community-based frameworks, APIs, and customizable threat detection policies. You can also find various SDKs and documentation for plugin development.
Falco is an IDS solution without preventive features, meaning your security team has to analyze the alerts manually. Deployment at scale can be cumbersome without extra automation tools, especially if you have thousands of microservices. It also has limited alerting configuration options for the same container types.
4. Prisma Cloud
Prisma Cloud (previously known as Twistlock) hosts a variety of tools for real-time intrusion prevention of Kubernetes environments. This solution offers virtual firewalls that inspect your traffic for high-risk content, allowing only safe traffic to enter. Its management tools and RBAC also let you establish secure network boundaries across your clusters.
The workload identifier feature assigns every container with a cryptographic identity. This way, the system blocks network access if the communicating workload is not verified or unauthorized.
On top of that, Prisma Cloud offers compliance checks to prevent misconfigurations in the application lifecycle. It has over 400 customizable checks for common regulations (including GDPR, PCI DSS, and HIPAA) and numerous pre-built compliance templates. You can also generate comprehensive traffic, application, and threat detection reports for compliance audits.
You’ll have to regularly apply new updates to the platform, which can result in reconfigurations and maintenance overhead. The platform would also benefit from more detailed technical documentation and responsive support.
5. Tigera Calico
Tigera Calico mitigates data breaches and advanced persistent threats with a rule-based engine and machine learning algorithms. It evaluates all traffic flowing through your microservices and generates alerts after detecting unusual behavior. Additionally, the networking plugin is easily scalable with minimum overhead.
It’s possible to configure the alerts to trigger remediation measures. For instance, the platform can isolate rogue microservices from your network and apply new security policies to block similar threats in the future.
You can capture malicious traffic and trigger in-depth analysis for known signatures with Honeypods (fake pods in your K8s cluster). Additionally, the platform offers advanced encryption for extra protection of sensitive data. A handy DNS dashboard also helps you confirm and eliminate connectivity issues in your cluster.
However, the installation is complex, as you need to deploy numerous namespaces with dozens of pods to deploy the solution. Besides, the architecture consists of multiple sub-projects, meaning troubleshooting can be a bit tricky.
6. Wazuh
Wazuh is a free, open-source platform for threat prevention in containerized environments. It uses a signature-based approach and a ruleset to look for compromise indicators and detect security violations. The solution also lets you analyze the configurations of your endpoints to reduce the attack surface of your cluster.
This platform comes with various incident response solutions to address active threats. It provides a robust search engine and visualization tool to help security teams process flagged incidents. In addition, the platform features security controls for compliance with industry regulations.
As for the downsides, Wazuh has a clunky interface and poor documentation. Plus, despite being free, tools like CIS-CAT scanning need external licenses. Finally, you must configure monitoring capabilities and alerts manually.
We should point out that any IDS and IPS product requires you to configure network policies, signatures, and baseline behavior for your cluster. Otherwise, you risk overwhelming your team with false alerts, overlooking real threats, or hurting your productivity by blocking trustworthy traffic.